With the Christmas holiday nearly here, many people are expecting new electronic gadgets under the tree. When connecting up new phones, tablets, laptops, and computers to the Internet, one should be mindful of some basic precautions to avoid identity theft, malware, and hacked accounts.
While the precautions outlined below require a few extra steps, they will help you avoid very unpleasant surprises such as:
- Discovering someone tried to transfer funds out of your bank account.
- Seeing your important passwords reset by someone stealing your identity through your email account.
- Finding your important files held for ransom, by a hacker demanding payment before possibly unlocking them.
Password Security
 The first line of defense you have for your online accounts are strong passwords. Too many people have weak passwords, often re-used across various web sites. Trying to hold many different strong passwords in your head is a non-starter for most of us.
The first line of defense you have for your online accounts are strong passwords. Too many people have weak passwords, often re-used across various web sites. Trying to hold many different strong passwords in your head is a non-starter for most of us.
The solution is to use a password manager such as 1Password where you only need to remember one strong (long) password, which safe guards all your other strong passwords, unique for each account.
For example, I’m currently using 1Password to hold nearly 200 secure logins for my various accounts. I have synchronized access to the passwords on my phone, tablet, and various computers. I can automatically create strong, unique passwords whenever I add a new account.
To further secure my accounts, I’m now even using secure passwords as the answers to those silly “security questions” some sites use for password recovery. For example, in response to What is your mother's maiden name?, I might enter 46elHBUZWRYHbuxTj4Kv. Much more secure than my mother’s actual maiden name, which could be discovered with enough leg work by an attacker.
Email Security
The next key precaution that everyone should be taking is to secure their email account. The reason is two-fold:
- If an attacker can login to your email account, they can quickly search your message history to find any account info you may have sent or received. This is invaluable for them to launch further attacks and try to steal your identity.
- If an attacker can read your email, they’ll try to reset your banking password for example. Often the bank will email them (you) a new password, as long as the simple security questions (like mother’s maiden name, probably found in your email) are completed.
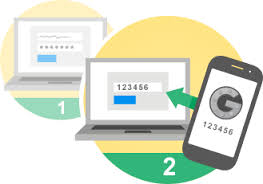 Naturally, you must have a strong password protecting your email account. However, I would also strongly encourage the use of two-step verification such as Google, Apple, Microsoft and others offer. Two-step verification ensures that access to your valuable email account is protected, not only by a password, but also a secret code, securely generated every few seconds on your phone. Two-step verification significantly raises the bar for a hacker to access your email.
Naturally, you must have a strong password protecting your email account. However, I would also strongly encourage the use of two-step verification such as Google, Apple, Microsoft and others offer. Two-step verification ensures that access to your valuable email account is protected, not only by a password, but also a secret code, securely generated every few seconds on your phone. Two-step verification significantly raises the bar for a hacker to access your email.
Phone Security
 Basics to stay secure with a smart phone or tablet these days include:
Basics to stay secure with a smart phone or tablet these days include:
- Setting a screen lock code, swipe pattern, or finger print. The data on your phone should not available to a thief if it is stolen.
- Use a password manager (as described above) to access secure, long, unique passwords on your phone. Don’t fall back to using short, easily-guessable passwords for accounts on your phone.
- Add your two-step verification app, such as Google Authenticator, to your phone to generate secret codes for logging into your email. Print out back-up codes and keep them safe in case you lose your phone.
- Keep up-to-date with any updates that your phone prompts you to install. Ensure they are legitimate updates, directly from the Google or Apple app stores.
- Use cloud services, such as Dropbox, Google Drive, or Apple iCloud, to back-up all critical data on your phone in case it breaks, is lost, or is stolen.
Computer Security
Similarly, to stay secure with a laptop or desktop you should:
- Use a screen lock timeout and a secure user login for your computer.
- Keep up-to-date with any updates that you are prompted you to install. Ensure they are legitimate updates from your OS vendor.
- Use cloud backup to preserve all your critical data in case your computer breaks, is lost, or is stolen.
Stay Vigilant
 If you’ve preserved and taken the precautions above, you’re already much safer than the majority of people using the Internet today. However, you should still remain cautious. Be wary of phishing emails and text messages that try to fool you into clicking.
If you’ve preserved and taken the precautions above, you’re already much safer than the majority of people using the Internet today. However, you should still remain cautious. Be wary of phishing emails and text messages that try to fool you into clicking.
Be mindful for suspcious-looking dialog messages on your computer, as they may simply be scam sites or apps trying to get you to contact them. Don’t! Talk to trusted family or friends before giving out any information to a random phone number.